Two Worlds Unite to Form Microsoft Endpoint Manager
It is a wonderful thing when new initiatives benefit both the company behind the implementation and the customers they serve. Such is the case with the announcement at Ignite 2019 that ConfigMgr and Intune are melding together to become one. Together, the idea is that they will form a single management conglomerate tool called Microsoft Endpoint Manager.
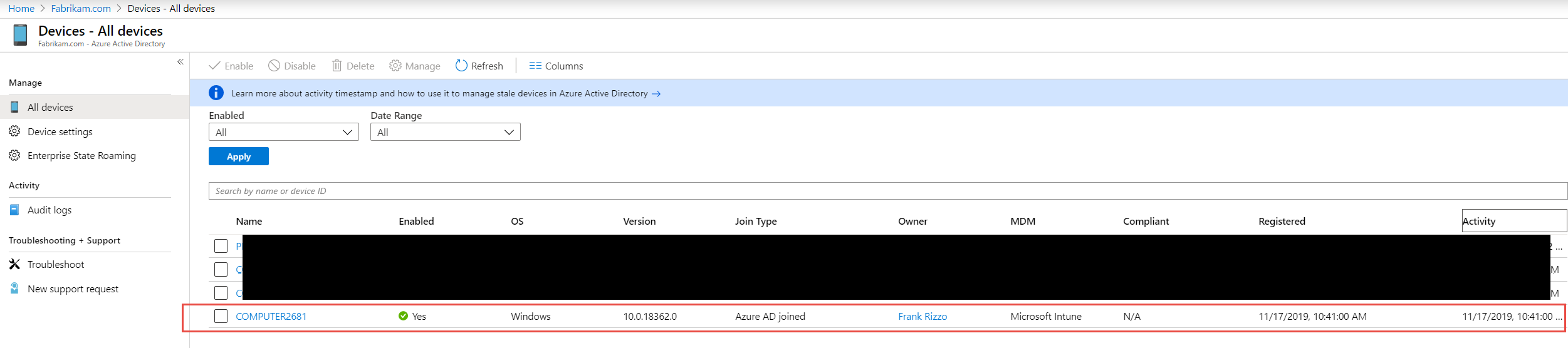
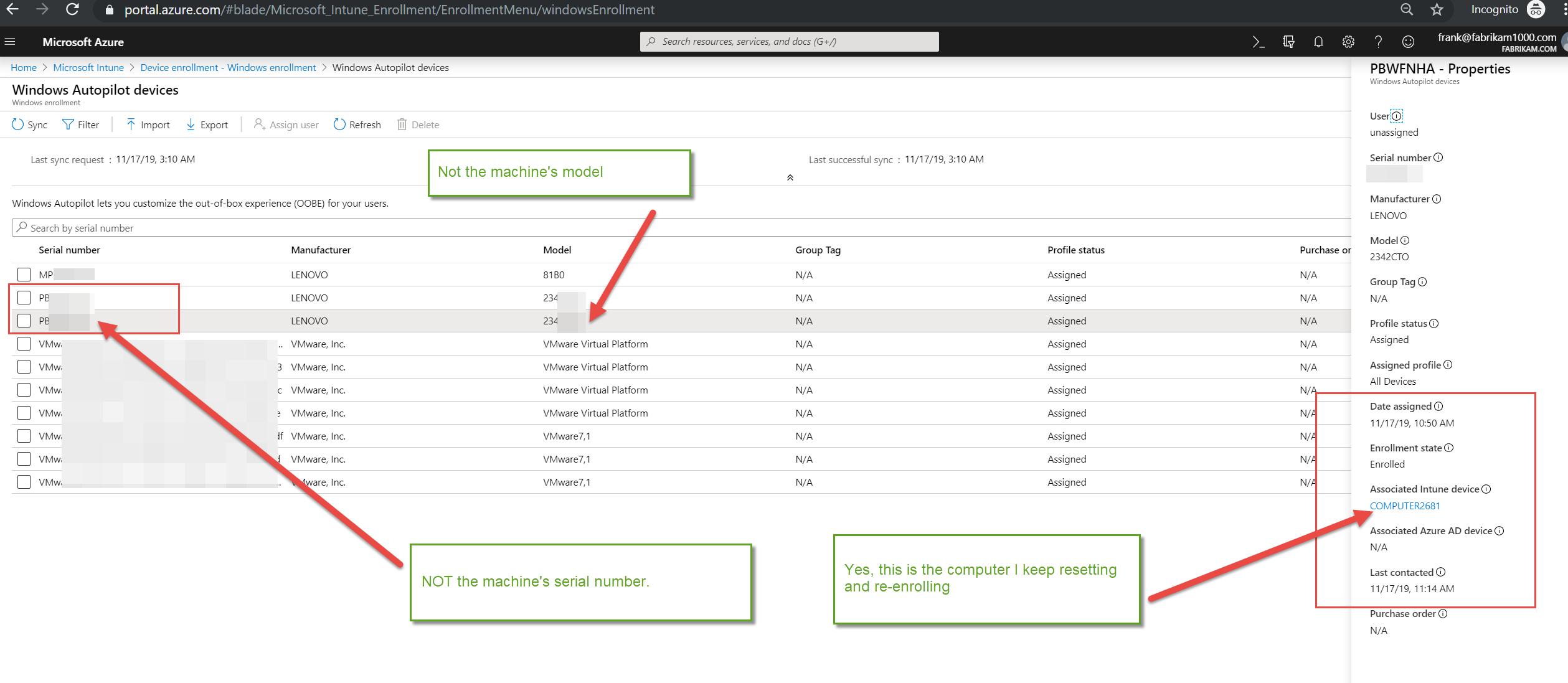
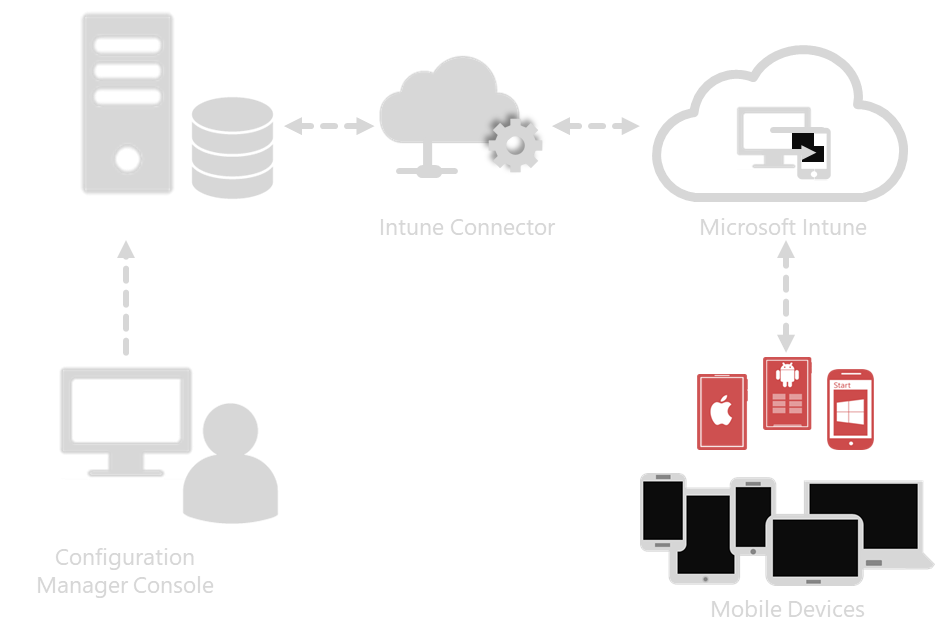
The MEM console will show a single view of all devices managed by either product through a single interface. Here's an example.
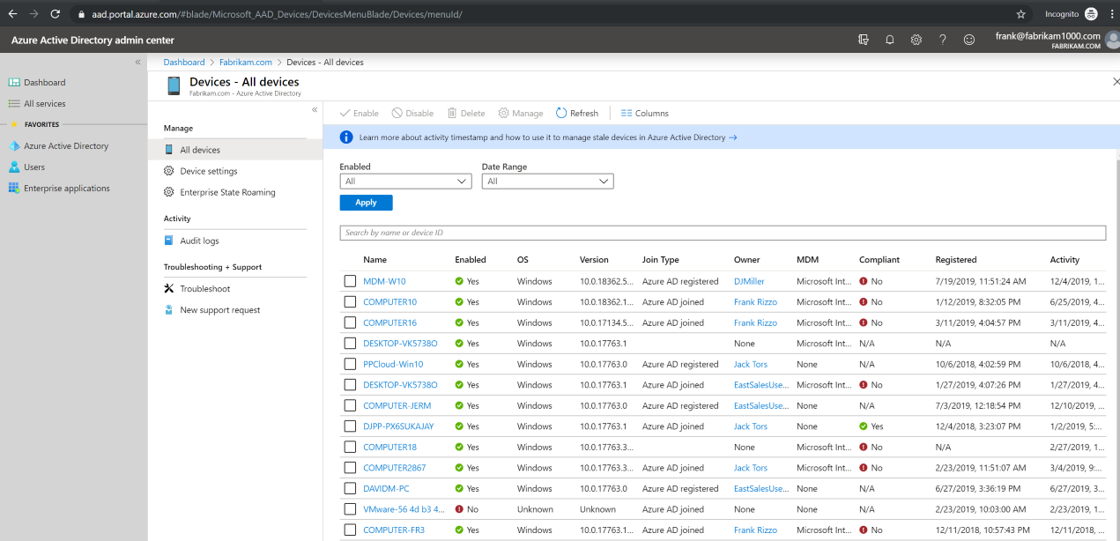
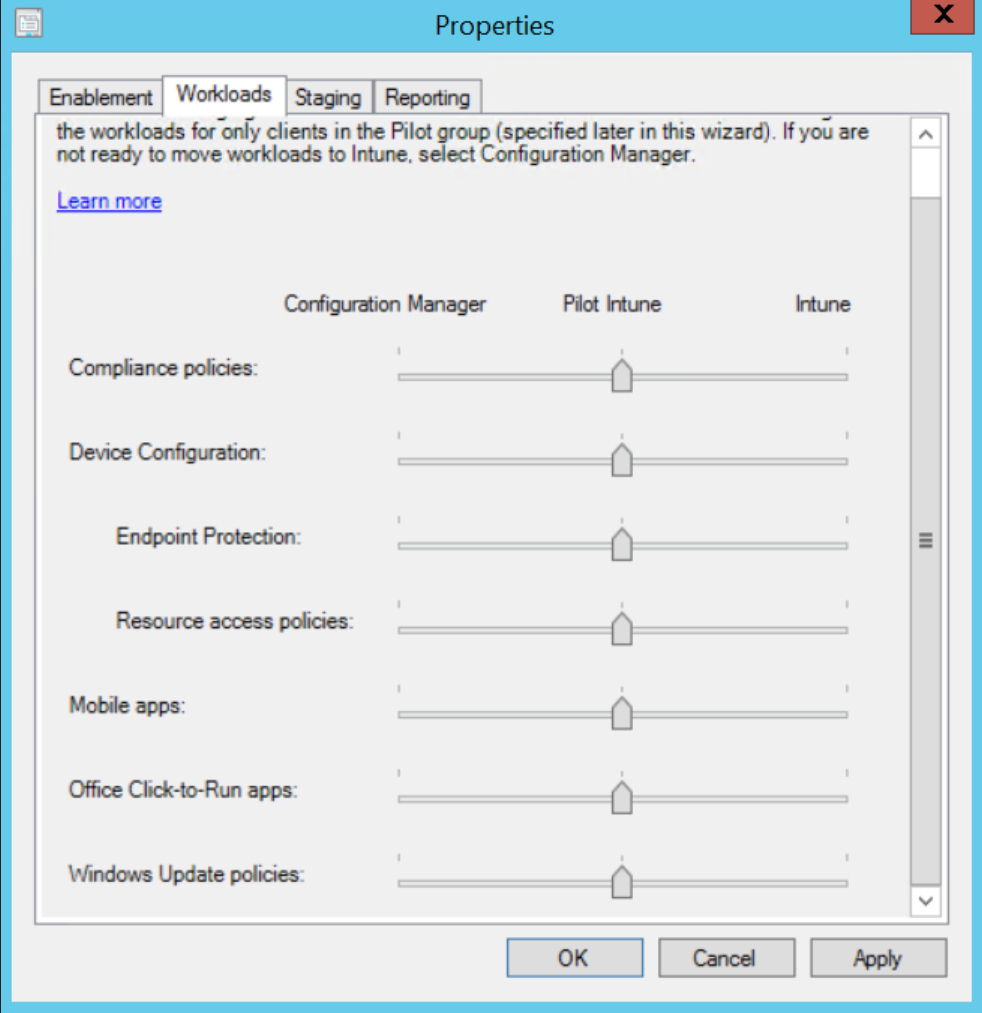
So the idea is that you can now manage ConfigMgr devices through the MEM interface. Of course, you can still manage through one or the other if you wish and there are some features that cannot be replicated amongst the two. Separately, the two tools will be known as:
- Microsoft Endpoint Manager Microsoft Intune (MEMMI)
- Microsoft Endpoint Manager Configuration Manager (MEMCM)
The merging of these two management systems now forms a new modern device management system that is exactly what internal IT needs to manage the modern workplace of today. Modern management for the modern workspace. That was a common theme at Ignite.
Branding and Licensing Simplification
Some may say that the merging is a recognition by Microsoft that vast majority of companies continue to stick to ConfigMgr and Group Policy to manage enterprise desktop devices. While Intune is capable of managing your entire Windows 10 environment, many companies continue to limit its management scope to mobile devices.
For Microsoft, bringing the two management systems together under one roof allows them to simplify their branding under one incorporated name. By integrating ConfigMgr into the Intune Portal itself, Microsoft is undoubtedly hoping that enterprises can better amalgamate themselves with the capabilities and functionality of MEMMI.
Users will enjoy the simplification of both licensing and experience. Those enterprises that currently have ConfigMgr licenses will automatically have Intune licenses too, allowing them to co-manage their desktop devices with both tools. From a product perspective, admins will be able to view their mobile devices and ConfigMgr controlled PC’s from a single interface. No more having to bounce repeatedly back and forth between interfaces throughout the course of the day. Says Brad Anderson, Corporate Vice President at Microsoft, “It’s all about simplifying — and we’re taking that simplifying deep and broad from a branding, licensing and product perspective,”
By implementing the new co-existing licensing model, Microsoft is encouraging those companies that need to need leave existing systems in place to provision new machines as cloud-managed devices. Regardless of how the device managed however, MEM provides a single view of all devices managed by either product.
Examining the Licensing Structure
So when you think of the new licensing model, think of the management scope of ConfigMgr. ConfigMgr specializes in PC desktop management, so your PC devices are now automatically licensed for Intune as well so you can go ahead and enable co-management if you want. Note: Phones and non-Microsoft devices are still the exclusive domain of Intune (MEMMI) so those devices are not applicable to receive dual licensing. Note you will still need Azure Active Directory P1 licensing for your users. Mobile devices, iOS and Linux machines will remain exclusively licensed under MEMMI.
Intelligence Driven
Modern management systems must be intelligence based in order to maximize the user experience. There are currently 190 million devices managed by either ConfigMgr or Intune. The convergence of ConfigMgr and Intune greatly scales the potential use of telemetry power that Internal IT can utilize in its PC deployments and problem solving. MEM will be introducing an array of intelligent actions that will give admins granular analysis as well as new comparative insights to their environments versus others.
One example of this is Productivity Score. Productivity Score will allow organizations to evaluate their employee and technology experiences into measurable metrics that Internal IT can use to justify the value that it brings to the organization. From the perspective of the user experience, it will quantify how people are collaborating on content, developing a meeting culture and communicating with one another. Real measured results concerning these types of user experiences can offer insights into how to enhance the user experience and increase productivity. The technology experience will provide insights into assessing policies, device settings, device boot times, application performance and adherence to security compliances
MEM is an Endpoint
Many of us predicted this would happen one day. As companies strive towards digitally transforming their organizations from the ground up, it was only a matter of time until something was done to streamline the management of on-premise and mobile desktops in scale. One point that Anderson emphasized his Intune presentation MEM is that the merging of these two management system giants is not a temporary arrangement. Says Anderson,
"Let me be very clear -- this vision includes both ConfigMgr and Intune. Co-management isn't a bridge; it's a destination."
MEM allows you to start utilizing cloud intelligence without making a single change to your ConfigMgr policies. Working collaboratively together, yet visible and accessible through a single interface, MEM provides the modern management system that Windows enterprises need. End-to-end management and automation is now available in a converged license package. Look for the MEM transformation to emerge within your Intune environment.