Microsoft Endpoint Policy Types Explained (Part 1)
Microsoft Endpoint Manager (the Intune part), is a powerful device management and endpoint security system that is constantly evolving. What began as a portal to manage and secure mobile devices can now manage desktop computers, virtual machines and even servers. It can now deliver a broad spectrum of configuration and security settings as well as intelligent cloud actions. Because of this, it’s hard to keep abreast of all of the changes and informational resources are perpetually outdated.
Microsoft Endpoint offers multiple policy types. With so much confusion out there concerning which policies do what, I thought it might be a good time to take a snapshot of the state of Microsoft Endpoint as it is today. This two-part series will cover a quick review, (or for some an introduction), on the various parts of this rapidly expanding management ecosphere.
Configuration Profiles
This has long been the bread and butter of Intune. Configuration policies are the equivalent of Group Policy Objects. A configuration profile is created to deploy managed settings to targeted devices or users. Like other MDM solutions, Microsoft Endpoint supports more than just Windows. When you go about creating a configuration profile, you can choose between multiple platforms including Android, iOS, iPadOS, macOS and Windows as is shown in the screenshot below.
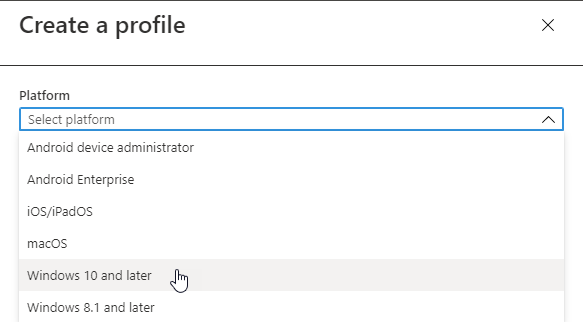
For the sake of this article, we will focus on Windows 10. You then select which profile type you want to configure settings for. The list of profiles has greatly expanded over the years. Some of the profiles available at this time include:
- Device Restrictions (Think Group Policy restrictions)
- Edition upgrade and mode switch
- Endpoint Protection
- VPN
- Wi-Fi
Below is an example of the available Control Panel Settings than you can block within the Device Restrictions policy.
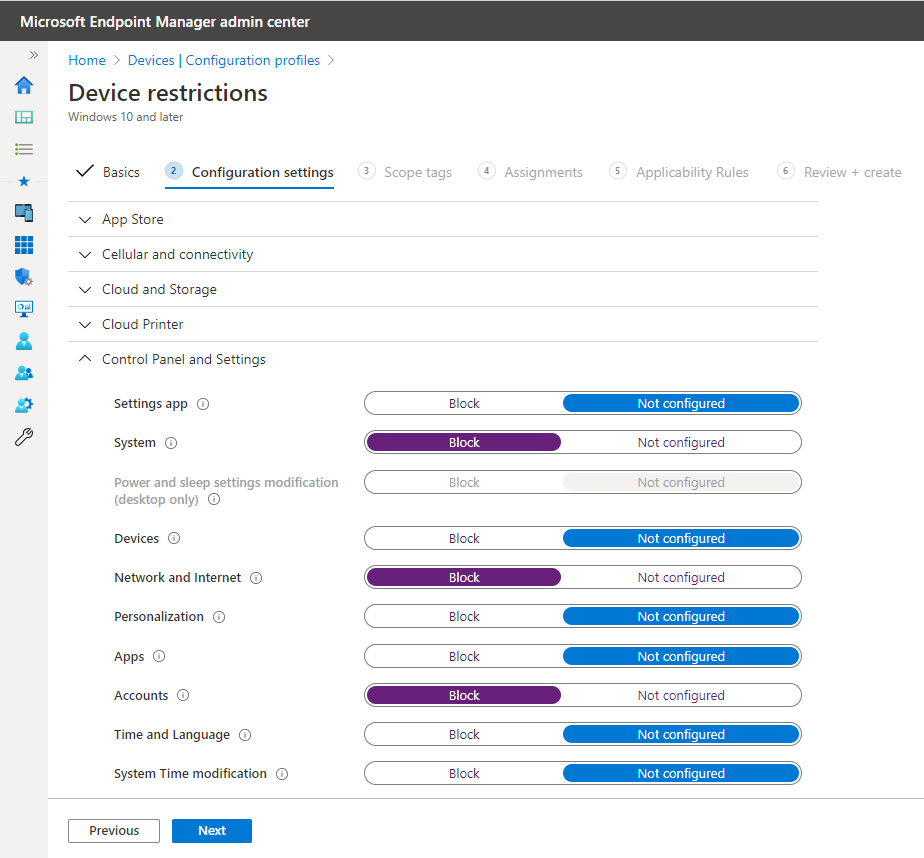
A wizard then guides you through the process of configuring your desired settings and deploying them to the applicable targets. While the number of available settings offered within Microsoft Endpoint has exponentially grown over the years, it still doesn’t come close to the more than 10,000 settings offered by the culmination of Group Policy and Group Policy Preferences combined. While its capabilities and offerings may fall short for on-prem AD enterprises, it does provide ample coverage for many mobile and non domain-joined devices.
Administrative Templates
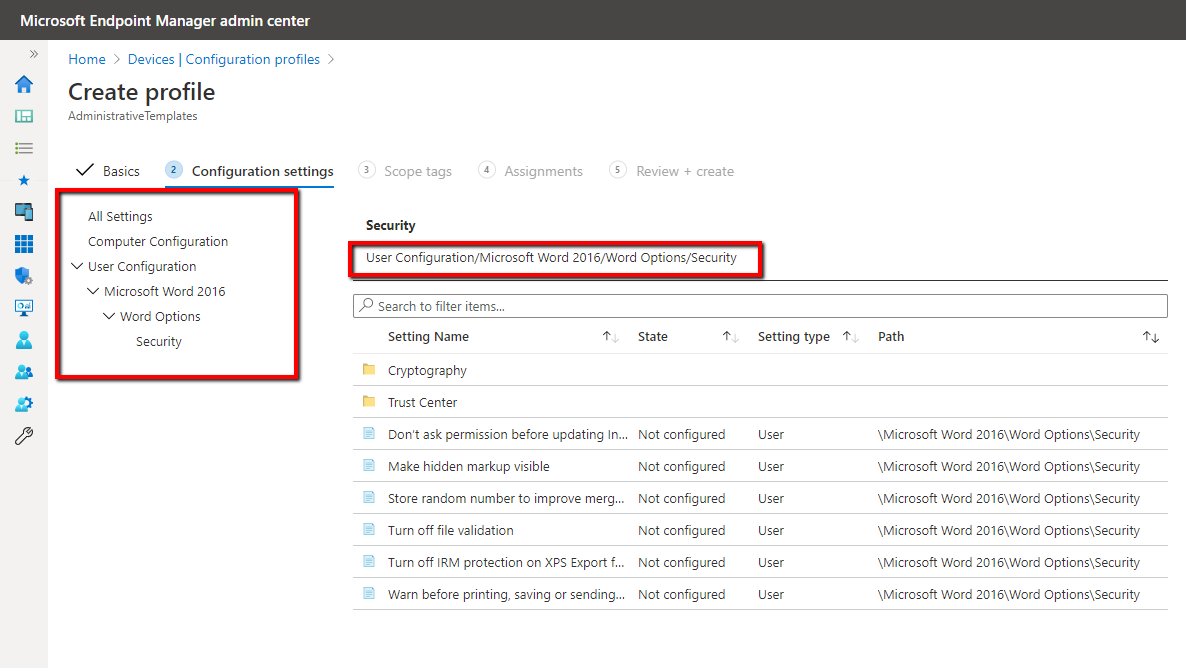
Administrative Templates is one of the available Configuration profiles but I want to focus on it separately. These are ADMX settings, some of the same ones you are accustomed to configuring in Group Policy Administrative Templates that includes both Computer and User side settings. Here you can configure settings for things such as Microsoft Edge, One Drive, Word, Excel, etc. In the screenshot below you will notice the same hierarchical structure you are familiar with in Group Policy Administrative Templates. Again, while the list of available ADMX settings has grown substantially, it still falls far short of what is currently available in native Group Policy. (Hint: Use PolicyPak MDM to take 100% of real on-prem GPO settings and use them with Intune.)
Custom Profiles
One more Configuration Profile type I want to focus on is Custom Profiles because a lot of people find them confusing. Windows 10 devices contain Configuration Service Provider (CSP) settings and it is these settings that MDM solutions actually manage. MDM has the ability to manage any CSP setting, but not all of these settings are currently built into the Microsoft Endpoint interface. That is where custom profiles come into play. If you want to deliver settings to an available CSP that isn’t accessible within the Microsoft Endpoint, you can create a custom profile which does require some input the following settings:
- Name: The name is for your own reference to help you identify it. Use any name you wish.
- Description: Enter a short summary of what the profile does and any other pertinent details
- OMA-URI: The OMA-URI settings are unique for each platform be it Android, iOS, Windows, etc. It is also case sensitive so be careful to type in the setting path correctly. To configure settings for a Windows 10 device you would type the path: Vendor/MSFT/Policy/Config/AreaName/PolicyName
- Data type: The data type will vary based on the OMA-URI setting. The options are String, String (XML file), Date and time, Integer, Floating point, Boolean and Base 64 (file)
- Value: Here is where you associate the OMA-URI value you wish to enforce.
Below is what the Custom Profile creation process looks like in Microsoft Endpoint.

So that sums up our look at Configuration Profiles.
In case you want a more in-depth view of these, I suggest you check out my MDM book.... www.MDMandGPanswers.com/book where I give more details and examples.
In Part 2 of this series, we will look at the other policy types such as security and conditional access.




Comments (0)